Thu, 21 Feb 2008 12:09 PM
Cisco ASA 5505 vs Juniper SSG 5
Michael Dale
I thought it was about time I did proper review of the Cisco ASA 5505 and the Juniper SSG 5.
Both devices are at the low end of firewall security devices offered by Cisco and Juniper.
The ASA 5505 is part of Cisco's new range of Adaptive Security Appliances (ASA) the replacement for the PIX. The 5505 replaces the old PIX 501 and 506e.
The SSG 5 is Juniper's lowest end Secure Services Gateway (SSG). The SSG 5 replaces the old Netscreen 5GT.
There are many models of the SSG 5 and ASA 5505 available, for this review I will be looking at the non wireless SSG 5 256mb version and the unlimited user ASA 5505 K9 version.
Before we get started I should make it clear that I work with the Juniper range of hardware every day; so I may be bias.
Overview
The first thing I'll do is compare the two devices "on paper".
| Cisco ASA 5505 | Juniper SSG 5 | |
| Model | ASA5505-UL-BUN-K9 | SSG-5-SH SSG5 RS-232 256MB |
| RRP* | $AU1,681.90 inc GST | $AU1,125.00 inc GST |
| Firewall Throughput | 150 Mbps | 160 Mbps or 90 Mbps of IMIX** traffic |
| VPN Throughput | 100 Mbps | 40 Mbps |
| Sessions | 10,000 | 8,000 |
| Connections/Second | 4,000 | 2,800 |
| Packets Per Second (64 byte) | 85,000 | 30,000 |
| IPSec Tunnels | 10 | 25 |
| SSL Tunnels | 2 | N/A |
| Memory | 256 MB (upgradable) | 256 MB |
| Flash | 128 MB (upgradable) | 64 MB (fixed) |
| Ethernet Ports | 8x100 Mbps (2 of which are PoE) | 7x100 Mbps |
| USB | 3xUSB 2.0 | 1xUSB 1.1 |
| VLANs | 3 (trunking disabled, DMZ Restricted) | 10 |
| OS | ASA 8.0(2) - ASDM 6.0(2) | ScreenOS 6.1.0r1 |
| Users | Unlimited | Unlimited |
| Routing Protocols | RIP v1/v2, OSPF, EIGRP | RIP v1/v2, BGP, OSPF |
| Anti-Virus | No (possible future) | Yes (paid for subscription) |
| Deep Inspection | Yes | Yes |
| Anti-Spam | No (possible future) | Yes (paid for subscription) |
| Console | RJ45 | RJ45 |
| Dialup Modem | No | No (external modem can be connected via the AUX port) |
| IPv6 | Yes | Yes |
* RRP based on Ingram Micro's pricing
** IMIX traffic is more demanding than a single packet size performance test and as such is more representative of real-world customer network traffic.
The IMIX traffic used is made up of 58.33% 64 byte packets + 33.33% 570 byte packets + 8.33% 1518 byte packets of UDP traffic.
So on paper the ASA 5505 has much better throughput and general hardware specifications, yet the SSG 5 supports more VPN tunnels, VLANS and has full UTM (Unified Threat Management).
The ASA 5505 is also about 50% more expensive (based on the retail prices), saying this wholesale prices of the two devices only differ by about $250 ext GST.
Cisco ASA 5505 out of the box
The ASA 5505 comes with the following:
- ASA 5505
- Power Supply
- Getting Started Guide (Software Version 7.2)
- Rollover console cable
- 90-Day Hardware Warranty
- Software and Documentation CD (Software Version 7.2)
- Regulatory Compliance and Safety Information Booklet
- 2 Ethernet Cables
Juniper SSG 5 out of the box
The SSG 5 comes with the following:
- SSG 5
- Power Supply
- Serial to RJ45 connector
- 1-Year Hardware Warranty
- 90-Day Software Warranty (from the date of shipment)
- Free download of the latest ScreenOS for the first 90-Days
- Software and Documentation CD
- 1 Ethernet Cable
- Desk Stand (allows the SSG 5 to stand upright)
The 90-Day software download for the Juniper device means that you can have to the latest software when you first purchase the device. Unfortunately this time period starts from when the device leaves Juniper. So if you purchase the device from a reseller the software update period may have already expired. This is still better than Cisco that requires you to purchase a SmartNet agreement before you can download anything.
The 90-Day Cisco hardware warranty is also a bit rude.
Cisco ASA 5505 Starting it up
Out of the box the ASA is setup with Ethernet0/0 being the WAN side while the rest of ports are setup as the LAN side. The default IP address of the box is 192.168.1.1.
If you're running an internet connection where an ip address is handed out via DHCP then the ASA will give you basic internet access straight off, although most of the time you'll want to configure PPPoE or something.
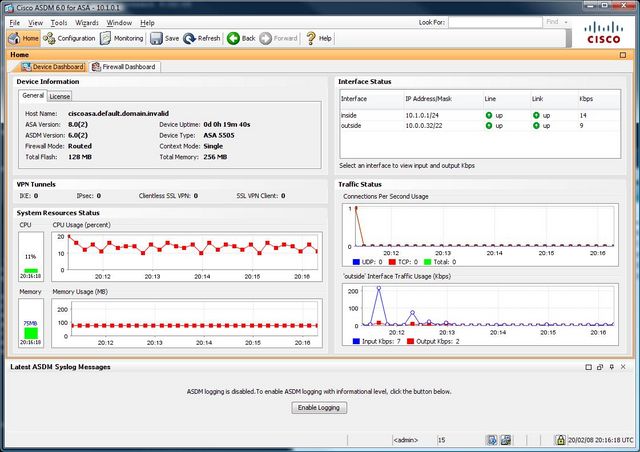
For users who have not used Cisco gear before then the easiest way is through ASDM (Adaptive Security Device Manager), cisco's GUI setup interface. To access this browse to https://192.168.1.1/ and download the ASDM.
Once started you are greeted with some statistics of the ASA.
ASDM is up to version 6 and is it now fairly comprehensive; if you don't like the command line then most of the configuration can be done here.
By default the ASA blocks and filters certain traffic for example ICMP is blocked.
Juniper SSG 5 Starting it up
Out of the box the SSG 5 is setup with Eth0/0 being the WAN side, Eth0/1 being the DMZ and the rest of the ports being the LAN side. The default IP address of the box is 192.168.1.1.
The SSG 5 uses zones.
"A security zone is a collection of one or more network segments requiring the regulation of inbound and outbound traffic via policies. Security zones are logical entities to which one or more interfaces are bound."
So what Cisco call VLANs (or Security Levels) are basically what Juniper call Zones.
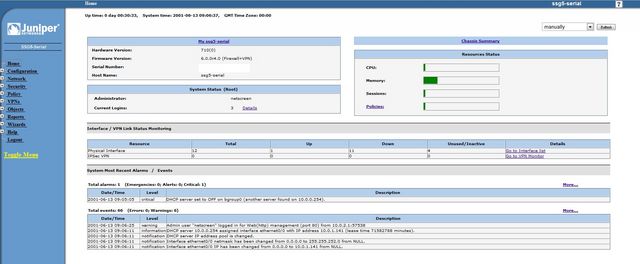
The SSG is managed through a web interface this can be found at http://192.168.1.1 (default username and password: netscreen).
Once you've logged in you are greated a general overview of the device.
Like the cisco device the SSG also allows configuration via the command line; although the WebUI is much more complete than the Cisco ASDM.
Personally I do most of my configuration in the WebUI.
By default all outbound traffic is allowed and the WAN interface (or Untrust as Juniper call it) is set in NAT mode. The Untrust interface isn't setup to receive an address via DHCP by default.
Cisco ASA 5505 The Hardware
The physical construction of the 5505 is very good. The outside casing is mostly plastic, while the base of the system is metal. The only point of concern is the power connector; it seems a bit flimsy and could be easily broken.
If you open up the 5505 you can see that both the flash and ram is upgradable. The flash is just a standard compact flash card, while the ram is PC3200 DDR UB NON-ECC CL3 DIMM 2.5v or 2.6v. It looks like the ASA 5505 can support up to 512mb of Ram.
The primary CPU is based on an AMD Geode chip, plus there is a hardware acceleration chip too (for VPN encryption etc).
The 5505 also has a Security Services Card slot allowing extra functionality to be added on. Although there are not any cards at this stage.
There are 2 USB 2.0 ports on the back and 1 on the front. Seems like a lot for a firewall! At this stage they don't do anything.
The inclusion of two Power over Ethernet ports is a great idea as it allows you to simply plug an IP phone in without the need for an extra power brick.
There is an internal battery that can be replaced if required.
Overall the ASA 5505 feel like it was built to last.
Juniper SSG 5 The Hardware
The physical construction of the SSG 5 is good, but it isn't has good as the 5505. My main point of concern is the single USB port on the back. It isn't attached to the outside casing and just feels a bit flimsy.
The SSG 5 allows for the memory to be upgraded, although 256mb is the max. I tried a 512mb DDR2 SODIMM in the device but it didn't boot. It is possible that I was using the wrong type of ram (on second look it may need DDR1). The flash memory is soldered onto the board and cannot be replaced.
The SSG 5 uses an Intel IXP455 chip running at 533MHz.
There is a single USB 1.1 port on the back of the device that can be used for storing log files or other firmware.
Cisco ASA 5505 The Software
At the time of writing software version 8.0(3) is currently the latest version for the ASA. Unfortunately I currently only have 8.0(2), saying this the differences should only be bug fixes.
The ASA software is simply a continuation of the PIX software. The configuration is stored in a single text file. With each version of the ASA/PIX software the command line configuration is slowly becoming more and more like Cisco IOS which is not a bad thing.
The ASA has a stack of features for a device so small and cheap. It does everything that the PIX 506e does (IPsec VPN, SPI firewall etc) plus more (SSL VPN, EIGMP). The inclusion of SSL VPN means that this device can easily support teleworkers that may not have access to an unrestricted internet connection. SSL VPN gives the end user an option of a client based connection (similar to an IPsec VPN) or a clientless connection (a web portal to published files and services).
The ASA 5505 also provides basic routing and nat functionality, meaning that you can run this device without a separate router. Unfortunately there is no option for an integrated ADSL modem, so a modem will need to be purchased.
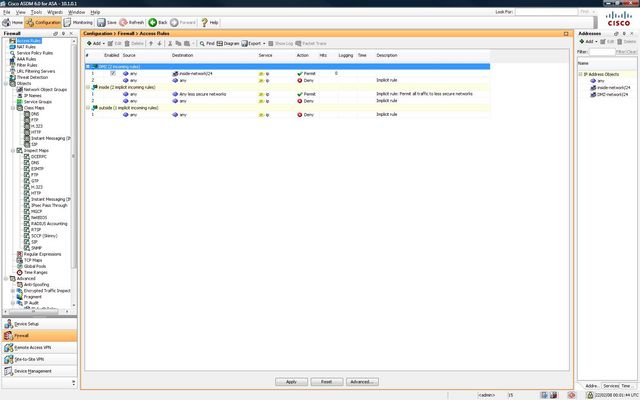
The configuration of the ASA can be scary for new users. ASDM is not particularly well laid out. NAT rules are in a different location to access rules and everytime you want to make a change you must save and upload the configuration again. The base license is also restrictive, you are limited to three "zones": untrust, trust and dmz. You cannot create pin holes in the DMZ to allow access the the Trust network either.
The SSL VPN is also very limited as you are only allowed 2 SSL VPN connections. IPsec is a little better with 10 tunnels allowed, but even cheap SOHO routers can do 10 IPsec tunnels.
All of these limits can be removed or increased with more expensive licenses, but they are much much more costly.
It is possible to get the ASA 5505 in 10 and 50 user versions (number of computers using the internet behind the ASA). Why Cisco have this limit is beond me. I've never seen a cheap SOHO router with a user limit.
The reporting options in ASA 5505 are fantastic. If you want to know what is going on it your network then the ASA will tell you. It can display the most used services, sources or destinations in a pie chart (plus a whole stack of other options).
Overall the ASA software is good, but there are far too many limits on the base 5505.
ASA Software Version 8.1 is due soon although I've yet to hear what extra features it will include.
Juniper SSG 5 The Software
The SSG 5 came out with ScreenOS 5.4 but since then Juniper have released 6.0 and 6.1 both adding lots of extra functionality. ScreenOS supports just about any routing protocol (BGP, OSPF, RIP etc) and has some really nice features that aren't found on the ASA 5505.
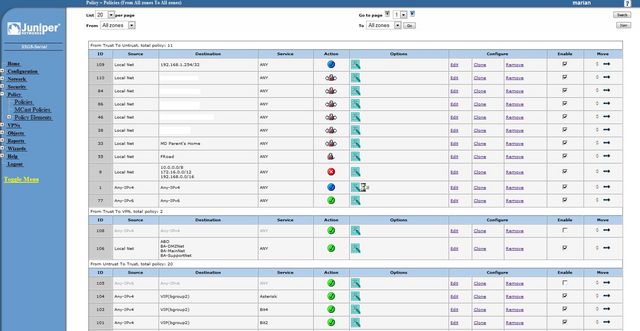
The base SSG 5 license supports unlimited users, 25 VPN tunnels and 10 zones. The extra zones really makes the SSG 5 stand out. For example you can have a Untrust, Trust, DMZ and VPN zone. All VPN tunnels can be bound to the VPN zone, separating it from internet traffic. There are also no limits on how the zones work so the DMZ can talk to the any zone if you so wish. With 10 zones every port on the SSG 5 can be part of a different network. So if I wanted to add a wireless access point I could create a zone that only allows the wireless users to access the internet.
Policy management is also much better than the ASA. Every change made via the web interface is automatically saved. You can quickly disable policies and move them around. You can fine tune each policy. For example you might want to enable NAT on a policy, or add anti-spam scanning on certain incoming SMTP connections. The policy management on the SSG 5 feels much more mature.
Again the SSG 5 like the ASA 5505 can be used as a stand alone device without the need for an extra router. The SSG 5 does have another nice option, you can purchase them with ADSL2+ modems built in (or ISDN or 56k modem). So you don't need to buy an extra modem. Saying this I find it easier and cheaper just to use an external modem as it can be upgraded if a new technology comes out.
ScreenOS 6.0 added Auto Connect VPN which works the same as Cisco's Dynamic Multipoint Virtual Private Network. This basically means that in a hub and spoke vpn setup the spoke sites (remote offices) can automatically establish a VPN tunnel between each other (based on the rules at the hub) to reduce the traffic going through the hub. This can increase bandwidth and decrease latency.
ScreenOS 6.1 added IKEv2 the next version of the Internet Key Exchange protocol which is used in IPsec.
UPDATE: Power Adapter
Just thought I'd add a quick section on the power adapter.
The Cisco ASA 5505's power adapter is quite large and seems to make a bit of noise (more than the device itself).

Conclusion
Both devices are fantastic yet each have their own strengths and weaknesses. For example the SSG doesn't support SSL VPNs while the ASA doesn't support built in Anti-Virus or Anti-Spam.
I feel that the ASA 5505 is a little let down by its software and licensing limits. The reporting options in the ASA are much better then the SSG, but this doesn't make up for its other short comings. SSL VPN is nice but again far too limited with only 2 connections. The ASA 5505 hardware is clearly better than the SSG 5: PoE ports, USB 2, higher throughput.
On paper the SSG 5 isn't has good as the ASA 5505, yet the device is much less limited. I personally don't feel that the performance of the SSG 5 isn't an issue. These two devices are designed for small businesses and teleworkers, they're never going to see 150mbit/sec of traffic.
The SSG 5 comes with many more hardware options, you can even get a version with 802.11a/b/g wireless.
To me the SSG 5 makes a better router than the ASA 5505. While the ASA 5505 makes more sense for a business with teleworkers that require SSL VPN.
The SSG 5 can handle more VPN tunnels (up to 40 with an extended license) and has some technology that makes it better for site to site VPNs, such as running BGP over an IPsec tunnel.
If you're currently running a Cisco network stick to the ASA. Likewise if you're running a Juniper network use the SSG.
For new users you need to decide on what is important to you. Do you plan on using SSL VPN? Then get the ASA 5505. If you're just using IPsec or require some more complex networks/routing get the SSG 5.
Value for money? The SSG 5 is better as there are far less software limits.
Comments
This is a very informative write-up, thanks for sharing! Most of my firewall experience has been with Cisco's PIX / ASA boxes. We are currently looking to buy a pair of firewalls mainly for LAN-to-LAN tunneling, but also for remote VPN capabilities so we were leaning towards the ASA 5505's just because I knew about them. A network engineer acquaintance recommended we check out the SSG 5. I believe in buying the best product for the job, rather than always sticking with a particular brand just because it might be marketed better. Your review reinforces that idea so we're going to try and demo the SSG 5 soon.
1: Comment Link
Hi Chris,
Thanks for commenting.
Let me know how you find the SSG 5.
2: Comment Link
A little clarification on the ASA:
With the Security Plus license, the number of VLANs goes to 20 (and VLAN trunking is enabled) and the number of VPNs goes to 25. Even better, the VLANs can talk to each other, so the DMZ functions as expected. Other parameters also increase.
Also, you can purchase more simultaneous licenses for the SSL VPN, but it gets expensive fast.
Personally, I always recommend the Security Plus license if I'm recommending an ASA so I don't run into any licensing gotchas that are different from the bigger ASAs.
Anyway, thanks for the comparison!
3: Comment Link
Thanks for the comment Clay.
Yes you're right. The SSG 5 also has an extended license that increases the VPN limit to 40, ups the sessions to 16,000, has 20 VLANs and allows for full active/active failover (which the ASA 5505 won't do).
4: Comment Link
Right, the ASA5505 will only do Active/Standby Failover. I've wondered about this though: how many offices are small enough to buy one of these low-end devices and still want to spend that much on *hardware* failover? I've yet to configure this on an ASA5505. The only clients I configure this for have 5510s or bigger.
I suspect this feature is far more of a "well, the competition has it, so we have to have it, too!" feature.
5: Comment Link
Thanks for the great review. I love the PoE ports in the ASA5505 and the larger power supply is needed for PoE requirements. Zero issues with the power supply and connectors...have been using the ASA for over a year. I personally feel ASDM is very clean and intuitive although I have not played much with WebUI. When you get a chance, run the packet tracer tool and the packet capture wizzard. Really cool utilities that take care the "what if" and other troubleshooting issues. I hear Juniper is getting rid of ScreenOs. Hopefully, the new JunOS that replaces ScreenOS is mature enough to provide as good service as ScreenOS.
6: Comment Link
We recently got 5 SSG-5 units for use at our remote offices off campus.
Do you know of a good source for documentation for the SSG-5s?
I find the documentation that Juniper sent with the units to be a little
lite on the details and examples of how to set these units up. I have
a case open with them but I would really like to not have to rely on
opening a new case anytime I need to configure something. Any
help would be appreciated. Thanks.
7: Comment Link
This would be the best place.
8: Comment Link
You can find SSG-5 books in book store or in google books.
http://www.google.com/books?id=oRLniDWYwrMC&printsec=frontcover&sig=EeT0X8fUAnEs28Yx8jCxZr2Q7jA
By the way, I'm using SSG-5 for last 6 months, and I got to know Juniper cusotmer support is very nice.. But my SSG-5 has downed more than 5 times already, and took RMA once!!!
9: Comment Link
Hi,
Is there a simple way to enable Large ICMP on the SSG5's?
I have one at each end of a VPN to a satellite office, but things such as Group Policy is disrupted by the ICMP issue.
Thanks
10: Comment Link
I have just replaced 100 SSG5 with ASA 5505s. SSGs performance numbers are drastically over exaggerated and the more features that are enabled the box starts to crawl. It does not handle AES 256 and maintain decent throughput, extremely frustrating! Also the Juniper help desk was poor and let my cases just drop off of the map. SSGs will be end of lifed shortly as they will not support JUNOS which is the stated direction and is where al of the feature development is going. This is a deadend box.
11: Comment Link
Hi Mark,
Thank you for you post, I do hope it is legitimate seeing that it has come from a Cisco IP address.
Personally I haven't had any issues with performance; and it will be many years before Juniper stops supporting the SSG range.
I'm sorry your experiance with Juniper wasn't good.
12: Comment Link
There will be active development of ScreenOS all the way until 2015.. and support for ScreenOS up until 2020. The SSG5's will not be discontinued anytime soon, it is only the larger versions of the SSG family that are going to be running Junos (and this is an option and not mandatory... for example an SSG 320-M - the M stands for Multi-OS, you can pick either Junos or ScreenOS whichever you prefer). Those little boxes are pound for pound some of the best firewalls on the market.
13: Comment Link
I'm Curious to know something...the ASA 5505 doesn't state any limitations on how many access-lists (security Policies for the Juniper folks) it can have. The SSG 5 is limited to 200 security policies (access-lists). For those of us that have a bigger home network this is kind of an important piece of item one should note.
14: Comment Link
I saw the nortel 222 router for even 1/2 the price of the SSG 5... is it possible to have someone comment on this...
We are tight on budget, and it seems to work well, we purchased 7 to trial (no wireless option though)
15: Comment Link
I just did a bit of searching. The nortel 222 router is a much cheaper and less featured router.
It doesn't support BGP/OSPF,Anti-Virus or Failover by the looks of it. It is also much slower. 20mbit VPN throughput vs 40mbit on the SSG and even more on the ASA.
Saying this it is probably suitable for most smaller networks.
16: Comment Link
Great comparison and thread - quick question:
Can the asa5505 be centrally managed, can I push policies or configurations remotely?
17: Comment Link
Sorry I'm not sure about the ASA, I know you can do it with the SSG using an extra piece of (expensive) software.
18: Comment Link
With the ASA you can push configs using something like Winagents HyperConf or Solarwinds Cirrus, just like many other devices that support terminal sessions. I'm not sure if there is a Cisco utility for doing this or not.
Either way, I love these ASA 5505s. They are unbeatable in performance and flexibility. The ASDM (monitoring and configuration GUI) is amazing and has every kind of info you can possibly desire. I've deployed about 20 of these for large and small customers, used them as edge firewalls, internal site-to-site VPN endpoints, and in other configurations and they are outstanding.
19: Comment Link
Working for Cisco I should be rooting for the ASA, but the truth is I think that the Juniper line of firewalls are soon going to pass Cisco by. I started with the Netscreen line before juniper bought it and have used all the netscreens up to the juniper 5000 series (Very much enjoyed the 5gt for home use), and have extensive experience with cisco and check point. Being a bit of a command line junkie I have to say I find the juniper command line structure well thought out and easier to use then the pix. Plus I like that a few very powerful options are not available in the Juniper GUI for some one to play with in the event some junior and (some times) senior SecAdmin forget to log out a session. The hard ware issue is a moot point once you get past the SOHO appliances and I feel is not a big deal in this instance. There is a good reason juniper over took nortel for the number 2 spot, and if cisco doesn't watch out maybe the 1 spot at least in firewall appliances.
I can't wait to get a ssg 5 for my home.
20: Comment Link
What a great review, thanks!
21: Comment Link
Does the SSG 5 allow for dynamic site-to-site VPN Tunnels using a DDNS host name rather than the IP Address? This is one drawback as far as I am concerned with the ASA. I mean YES in a perfect world each of your sites should have a static IP but it is not always offered depending on the location/carrier. I was just wondering... Great review BTW... I have been looking for something like this...
22: Comment Link
You can have standard site-to-site VPN using a DDNS host name. But I'm not sure if you can have a dynamic site-to-site VPN.
23: Comment Link
You can definetly have dynamic VPN's with ASA5505 with any cisco device. Integration with Juniper is the problem, why would you need a Peer-ID ? you have the IP address already.
24: Comment Link
If you are not sure about which one to go for, and need some more independant advice, Gartners report on Enterprise Firewalls will certainly surprise a few people. I would include a link, but not allowed to - so google gartner and firewalls.
25: Comment Link
I've worked with Cisco products for many years, and I've done quite a bit of engineering on pix's and asa's from small to huge organizations. I've found plenty of flaws and bugs in the OS for pix's and asa's and I'm looking to move away from them. ASDM is a joke when it comes to a webgui although I have to say I'm a command line junkie myself. I have minimal experience with Junipers Netscreen product but after helping out a few customers with them and reading the documentation I was really impressed. From a network engineers stand point I need something that'll do auto failover for both wan services and VPN tunnels, along with Antivirus and spam filtering. I've found some great features when it comes to detecting WAN failure and failover that the Netscreen product had way before Cisco did on their PIX's/ASA's... although they had it on their 800 series routers. My biggest gripe with Cisco's line of security products is the lack of features that their routers have had for years (GRE tunnels that work correctly, WAN failover) and that they don't support antivirus/spam at lower end models when everyone else seems to be doing it at a reasonable price.
26: Comment Link
I have to work with round about 200 SSG5 systems since some day and the frist thing I remembered is, that it looks very close the Fortinet Fortigate systems, which we're prefere since some years. But maybe I will prefere the SSG next time, cause the bit cheaper listprice and the wide range of Juniper products. Just the CLI is different but I belive the roots are the same from netscreen.
I like cisco products too cause I can do so much with everything but the are mostly too expensive and also limited. I'm still interested in the ASA series but without AntiSpam, AntiVirus and so on, I would miss something and our customers too. And if you would buy a bigger ASA series, you just can add one module for anti-X but you have to miss the other features... is it so hard for cisco to integrate a second slot? And I have never seen a small company with maybe 5 people working in, which likes to buy a ASA 5510 with some modules for some thousend euro. If you like to use every anti-x solution which is integrated in the SSG series you have to buy round about 2 ASA 5510 - which small company will do that? It's a pity.
27: Comment Link
Has anyone used one of the Checkpoints UTM's like the UTM-270 ? or Edge product ? I am looking for a UTM for one of my sites and am thinking about the CheckPoint product. I am looking at the ssg320 or the UTM-270 checkpoint.
28: Comment Link
Then I would prefer the Juniper cause you get an appliance. For the CheckPoint you have to buy a Nokia appliance first or you need a server. In the IPS market, Juniper is leading with TipingPoint. UTM features from both are bought external like Kaspersky and co. Just the management from more then one system is better with checkpoint and it's central management. Cause we don't know which part is import for you and your customer, we can not tell you exactly what's better.
29: Comment Link
The most important part I am looking is the scanning features like antivirus,spam,spyware. Do you know if the SSG models will do any kind of load balance IF i an connecting a T1 and and cable model like Comcast for a back up line.
30: Comment Link
Ciscos ASSAs are for house-play only, i believe that cisco its good for router and switches, for security in the tests of security magazines dont evaluate Cisco, only Juniper, Checkpoint, sonic Wall, Fortinet.
i have SSG5 and Fortinet FG60B and i installed pix506e in the past, the FG60B its the leader very far from others.
The FortiIos its ScreenOS cousin, the end of ScreenOs its near, the 320M and SRX series are saying that, Juniper have to recover the leadership as past Netscreen in security appliances.
31: Comment Link
I've never played with ASA's before but just bought 2 x Juniper SSG-320M's for a client of mine. Truth be told, as it was my first time with a Juniper box I got in extra help (Paid).
I was amazed at how quick and easy it was to setup the Juniper firewalls. I've moved from Watchguard firewalls which were appaling for performance. The WebUI on Juniper is really easy to use and get to grips of, I picked it up in less than a day. In all honesty, the GUI looked a little too basic. Just seems like something was missing.
However, now I am looking for a new firewall for a datacentre install and am quite interested in the reporting bonuses of the ASA's. Yes, the Juniper's are quick and fast but there is very very little help when it comes to reporting and logs. Anyone care to comment or provide any feedback pls.
This is a head-to-head between Juniper SSG-320M and the Cisco ASA 5540. For a datacentre install, with VPN's. Real-life experiences would be useful.
Thanks.
P.S. Great posts.
33: Comment Link
Hi Harry,
Looks like ScreenOS 6.2 might have some better reporting options, but I think you'll need Network and Security Manager (NSM).
Some more info can be found here (under subheading Network and Security Manager (NSM)):
http://www.juniper.net/techpubs/software/screenos/screenos6.2.0/rn_620_r1.pdf
I haven't used it myself.
34: Comment Link
Hi Michael, thanks for the doc.
I had a look at the doc and looks like they have added bits to the Alarms and Auditing but I don't think that is significantly better. I guess I have been spoilt by the Watchguard logging system all these years and have become dependant on it.
One important but basic question I had was, can the SSG's run in transparent mode. i.e. have a no-NAT setup as our DC has all external IP's for all the servers. How would this be setup?
Any takers on the ASA's?
Thanks.
35: Comment Link
I just switched from ASA5505 to the SSG5 due to the DDNS feature available at home. However, after trying to setup site-to-site tunnels with multiple subnets ranges at home and at data centers....on both ends and securing them down with policies...I found out the true limitations of the SSG itself.
I can't protect the subnet ranges with tunnels nor can I create a good policy based vpn tunnel to replace the peer-ids (route based vpn tunnel). Juniper support was no help. Going back to something that I know works...Cisco.
36: Comment Link
I got some competitor tests from cisco and fortinet. Fortinet is talking about the Cisco ASA, that you can not use IPS and Anti-X at the same time and you don't have much models to choose and less port density. And the costs are in focus too.
Cisco on the other hand has competitor analysis too in the partner net agains fortigate systems. Cisco shows in some different performance tests, that the ASA Systems will not loos so much performance and thruput like the fortigate if you enable IPS and AntiX and so on at the same time. Then cisco shows some test for the antivirus engine, where the asa got absoutely better results from independent testcenters (virus100 and so on). Cisco tells, there is no use for saving money If you have a poor anti-X engine. Cisco uses TrensMicro.
I couldn't find some informations about the feature set on antispam in the Cisco ASA. Can anyone tell me which features I can enable like RBL filtering and so on? Or does it just work with the database from TrendMicro?
I'm lookint at this time for a NAC solutions too. Fortinet has it's 224B and 6xx Systems with a high port density like a switch. So we could use the complete set of anti-x directly on the "switch" - but if we loose too much thruput....?
Has anyone some more experiences with the cisco ASA Series?
37: Comment Link
>17. On Tue, 29 Jul 2008 at 12:13 PM, Steve wrote:
>Great comparison and thread - quick question:
>Can the asa5505 be centrally managed, can I push policies or configurations >remotely?
>18. On Tue, 29 Jul 2008 at 1:00 PM, Michael Dale reply:
>Sorry I'm not sure about the ASA, I know you can do it with the SSG using an >extra piece of (expensive) software.
Hi Michael, you can do it with a *free* piece of software : NSM (Network and Security Manager). The free license allow to manage up to 25 devices. This is definitely a big plus for the SSG5.
I work with Cisco / Juniper / Check Point firewalls, and I totally agree with the comment 20 : Juniper rulez !
38: Comment Link
Hi Fabien,
I had a look on the juniper site and couldn't see where to download the free version (I have an account).
Any ideas?
39: Comment Link
Hi Michael,
All the version of NSM are free ! A license is necessary only when NSM is used to more than 25 appliances :
"- If I am managing 25 devices or less, do I need a license?
- During a new installation, the NSM 2007.3 installer will prompt if you would like to use the NSM base license which supports up to 25 devices and HA mode. It is not required to obtain a license for 25 devices or less"
Source : http://kb.juniper.net/index?page=content&id=KB10480
40: Comment Link
Sorry for my errors in my previous email, you should read :
Hi Michael,
All the versions of NSM are free ! A license is needed only when NSM is used to manage more than 25 appliances :
"- If I am managing 25 devices or less, do I need a license?
- During a new installation, the NSM 2007.3 installer will prompt if you would like to use the NSM base license which supports up to 25 devices and HA mode. It is not required to obtain a license for 25 devices or less"
Source : http://kb.juniper.net/index?page=content&id=KB10480
41: Comment Link
Hi Fabien, I still cannot see where you can download this software.
The only item I can see on the url you linked that might be the software is NS-SM-S-BSE but this is listed at around $AU12,000.
42: Comment Link
Hi Michael,
Ok, I made a mistake : it seems that the software is not free (but there is no other cost until you manage less than 25 devices).
To download the software : go on juniper.net > Support > Download Software > NSM/Global Pro > ScreenOS Software Downloads : look for the entry Network-and-Security_Manager . You will be able to download all the software versions of NSM here (the last one is 2008.2). PS. : I have a Juniper Partner account.
43: Comment Link
Hi Fabien,
It doesn't look like the download is available to regular customers. You may have the link ONLY because you are a partner user account. I am, like Michael, trying to get hold of the software as we have about 5 SSG-320/350 firewalls which we want to manage.
I'm not sure about Junipers software distribution legalities, but would you be able to provide us with a direct link to the download location or even download/upload it for us... assuming it is allowed. ;-) I really need to get hold of this FREE software.
Thanks.
44: Comment Link
Someone asked if there was software to centrally manage Cisco PIX/ASA devices.
The answer is yes. Cisco Security Manger. VERY VERY Expensive. My company just started using it to manage our growing fleet of Cisco firewalls. I would NOT recommend this product for the ASA. The ASDM has a much better interface. We will be evaluating Juniper devices soon. I hope the NSM has a better interface.
45: Comment Link
to TMB:
Can you tell us, why your company is using so much ASA devices instead of SSG from Juniper? The running costs from cisco are a shame. The only great thing on cisco is, you will finde everywhere somebody who can help you and you can buy everything from cisco. From small business to big enterprise systems.
I bougth myself for a self study a cisco device for a while. Now we're friends but at the first month I could kick it in the trash with it's damed management. (Cisco 851)
46: Comment Link
Hi there!
It seems I've finally found a lot of IT professionals knowing both Cisco and Juniper equipment at this forum!!!
I need a device for my fix IP Ethernet, which will have three Macs behind it. One for development and Internet browsing, another one will collect data from a VPN channel listening on a single port and the third one will serve the browsing users on a redirected port 80. I'd like to have a port 5900 open for VNC (desktop sharing). It has to be well protected from attackers trying to slow down or disable my services.
I am a programmer, not a network specialist, and so I lack a lot of knowledge in the firewall/router field.
Can you tell me, which device (5505, 881 or ssg 5) is better suited for this setup?
In the user guide of the ssg 5 there are listed some features against DoS, DDoS, port scanning etc. It has an ISP too.
Can somebody give me a clue if 5505 is equipped with similar defense? And the cisco 881?
My another question is, which one is better matched to Mac OS X?
Any help appreciated,
Akos
47: Comment Link
We are rolling over from the old PIX platform.
I couldn't tell you why we are using ASA.
I will push to at least consider SSG for future firewall purchases...
We also use Checkpoint firewalls, so we are not a cisco-only shop.
48: Comment Link
I purchased an SSG 5 last year and find it completely confusing. I have tried and tried using their documentation to make VPN's work and understand how to configure zones to work on VLAN's and just plain find the device and Juniper's "terminology" frustrating. And calling JTAC is miserable because there is such a big language barrier - I have tried emailing with them but they rarely want to do anything via email, they always want a phone call during which I can't understand what is being said to me. I just wish I would find clear, concise documentation and setup instructions so that I could actually make my SSG 5 do what it is claimed to do.
49: Comment Link
to Darly.
If you have problems with your Juniper equipment, maybe you can ask the service team at your distribution. We do all with "computerlinks" and there are very good technical engineers. And they all can english too :o)
http://www.computerlinks.co.uk/unipalm/products/juniper/juniper_home.cfm
to Akos.
I think the ASA should be more easy for a non technical person.
But If would prefer you the Fortigate 50B. Costs round about 450€ inkl. all security features. The only think I will find better from Juniper to Fortinet is, that juniper partners with Kasperksy and the IDS system may be a bit better. But it's IDS only machines has an absolute different systems - that you can not ocmpare with the ids from the ssg series routers.
50: Comment Link
Hi Marco!
Thank you for your advice :)
It was really a difficult choice, but I finally went for the ssg-5. I adore to learn new things, so a more complex management didn't scare me :)
I realized I'll possibly need more virtual devices that available on a basic 5505, and it would be only available on the 5505 as upgrade for extra price, exceeding the 256Mb Junipers price. The other reason, I've found a really profound description of intrusion detection, exploit, DoS, scanning, etc. prevention in the Junipers manual while the 5505 seems not to have similar features. At least I wasn't able to find it in their manual, nor on the net. What I've found, were some forum comments about 5505 not having IPS, and it may get it via the expansion slot sometime in the future. As I'm not Bank Of England the protective measures of my ssg-5 will suffice :)
The another reason was a very friendly price offer from a local dealer:) I regret not having the SSL and MAC cloning capability of 5505 but I'll try to live with it.
Fortigate is not present here in Hungary at all! It is distributed to us from Poland, there is no local technical help, and products are available only to dealers, no end users. While one of the Juniper main distributors and a local dealer are just a few streets away, they are very helpful, and there is a local technical help-desk in hungarian on workdays!
At the start I had problems with the rapid deployment. After making a configuration with it, I couldn't establish a connection to my ssg-5 whatever IP address I tried! It didn't give an IP address to my PC and no gateway was displayed in IPCONFIG. factory reset, try again, but the same result. So I went for WebUI and had my Internet connection back in a few seconds. It was really easy with the WebUI! I don't know what was the issue with the rapid deployment... Now I'm enjoying my new firewall and learning the secrets of IT management :)
Have a nice day,
Akos
51: Comment Link
Does Anyone know if the 5505 will be introduced with a wireless option like the 871W. To go an buy an additional 521 Access point pushes the price well over 1000.00. these customer tend to bark at the price for a router/firewall device.
52: Comment Link
to Trevis:
I think, you will never see a ASA with integrated WLAN interface. Cisco is often building a device, which is best as it is and not a device which could be everything but nothing of them perfect or best in class. Maybe that's the reason for just one extension slot at the asa series... best performance for ids/ips or anti-x...
53: Comment Link
Unless you build lan2lans with the asa's or you use certs, you will be bond to user credentials with the Cisco 5505, hence the reason why Juniper uses peer id for dynamic tunnels. I went thru both options this year and i ended up with both (just because I don't have vpn ssl to eliminate the ASA). Cisco is your better bet for dumb down end user access, while Juniper's are more enterprise oriented. If anyone believes the performance numbers from Cisco they need a reality check. I can't understand how people look at the ASDM as say it intuitive, far from it imho. Support wise, Juniper is far better then Cisco any day (you might run into idiots anywhere at anytime). Command line the ScreenOS is far better and easier to work with, and troubleshooting commends are more intuitive. Keep in mind that at the end of the day the ASA its just a PIX on steroids.
54: Comment Link
to Michael Dale
I would love to see a competition between the SSG and an FortiGate. Both have the same roots and fortinet is building only firewall systems but tell heavy "max concurrent connection" values.
An Fortigate 50B for example you can receive as a demo unit for some weeks at a distribution. Maybe you can ask at your local computerlinks.com - they should have one.
Ah, about Cisco and Juniper i also found a great movie. That's interessting for somebody here: http://www.centracomm.net/blog/ssg-to-isr/
55: Comment Link
In that Cisco vs Juniper video they put up a 600Mbps device vs a 112.64Mbps device which seems pretty unfair to me. I'd love to see another test with two similar spec'd devices to see how they perform. A Juniper SSG 520 vs a Cisco ASA 5540 seems like much more fair since it would now be a firewall vs firewall.
56: Comment Link
Thanks for all valuable information.
I had experience with FortiGate 200A and FortiGate 60A. We had troubles to make DDNS VPN between both boxes. Anyhow, we are in process of selecting UTM and need your help in the following:
1) compression between Juniper, FortiGate, and CISCO ASA.
2) How is Internet browsing Performance with Juniper?
3) Which box performance better?
4) How is Virus scanning performance?
57: Comment Link
On base unit without add-ons, you can purchase the ASA5505 for $350 and SSG5 for $500.
58: Comment Link
ASA is a Firewall
SSG is an Integrated Service Router
Seems like a small difference but try routing multiple subnets over the same VPN tunnel on your ASA and see how far you get. Try to run OSPF over VPN on the ASA. None of those items work. Yet all the standard routing protocols on the SSG work wonderfuly well.
Shouldn't the SSG be compared to the 890 series? Routing on the ASA is just terrible. NO Gre tunnels either? I made a mistake of buying an ASA thinking it was a fully functional integrated service router. I assumed this based on reviews like this.
Be warned. the ASA is a firewall, a good one to but it is not a fully functional router/VPN router.
59: Comment Link
Hi fli,
I agree.
I did mention this in my review near the bottom:
"To me the SSG 5 makes a better router than the ASA 5505. While the ASA 5505 makes more sense for a business with teleworkers that require SSL VPN.
The SSG 5 can handle more VPN tunnels (up to 40 with an extended license) and has some technology that makes it better for site to site VPNs, such as running BGP over an IPsec tunnel."
60: Comment Link
Hi Michael,
A Juniper SSG5 v. Juniper SRX100 will be VERY interesting, isn't ? This new toy from Juniper looks amazing (JunOS powered !).
61: Comment Link
I also would love to see a SRX100 test at this page - maybe agains a Fortigate, ASA or SSG or just for it's own...
62: Comment Link
I currently work for a company with 50 users. We do not use an VPN. Would the SSG5 suffice or would you recommend a higher end SSG?
Thanks,
Brett
63: Comment Link
The SSG5 should be okay. How fast is your internet link? The main limiting factor on the SSG5 is the session limit of 8,000.
Personally I would use something like an SSG140 or SRX240.
64: Comment Link
Thanks for the speedy reply!
We recently got a T1 (1.544 Mbps). I might add that we are currently using a VERY old Netscreen-10 (when the company was Netscreen) which supports 4,000 sessions. Since getting the T1, on some systems, we are experiencing freezes during downloads and when receiving emails with attachments. Also, occasional errors such as "Connection closed by foreign host" and "The connection was reset". I also see a lot of RX errors on our switch port that the Netscreen-10 is connected too. I'm sure that 10Base-T half-duplex connection isn't helping as well. I've also done some testing with the Netscreen-10 out of the equation and everything is fine. I've been attempting to get a new firewall now for about oooohhhhh 6 years but now I think this is the wake up call management needs :-)
When comparing specs with the SSG5 it seems that it would be a good jump in specs when compared to the Netscreen-10 (http://www.interworld.net/netscreenspecs.html). Do you still believe the SSG140 or SRX240 would be a better fit?
Thanks again!
-Brett
65: Comment Link
The SRX range runs JunOS and is in the process of replacing ScreenOS. ScreenOS is still supported and will be for a few more years but no new devices will be coming out with it.
You should also look at the SRX100 and SRX210.
The SSG5 should be fine for a T1 link, I've pushed much more traffic than that through one. The SSG5 is a great device.
You can also get the extended license for the SSG5 to increase it to 16,000 sessions if needed in future.
66: Comment Link
Great. Thanks for your help! I'm currently looking at the SRX210.
67: Comment Link
Im a cisco path engineer, i woukd want ti know abot SRX240, what are the value added features compaired to cisco L3 switch.
68: Comment Link
does anyone actually test performance test, I wish I remember which ScreenOS I had but I upgraded to 6.2 then download to 6.1 recommend version, performance is very bad. without SSG, I get download of 25-30M with it, I only can get 2-3M top.
does anyone have similar problem ?
69: Comment Link
Hi Tatsuya,
It sounds like you have an issue with your SSG configuration. Possibly a Network Duplex issue.
The SSG5 can do 90mbits/sec in the real world.
70: Comment Link
Hello Michael ! great post, very useful information. Do you know if the SSG5 can
be converted to Junos ? thank youj
71: Comment Link
Hi Anonymous,
Thanks for the comment.
The SSG5 can NOT be upgraded to JunOS. It would be awesome, but it just isn't possible. JunOS requires lots more storage space and RAM.
The replacement for the SSG5 is the SRX100 and SRX210, both devices run JunOS.
72: Comment Link
To nhk,
SRX240 has not many switching features compared to any switch, since it is aimed to be a security services router in main use. ALso SRX devices have much more routing features, than any SSG before plus some layer features. Fro example you will have stp, rstp, mstp, you will have 802.1X, you will have GARP, LAG, Multicast and even bridge domains. and Q-in-Q on ports configured for ethernet switching. In QinQ you will have All-in-one bundling only for SRX devices. Anyway SRX cannot be compared to cisco layer switch in any way, maybe to some cisco firewalls, but having vpls on SRX with no additional cost , I don't think cisco firewalls can compare something that, maybe some cisco routers, but then the flow routing is absent there, so basically Juniper took his own way to build a good devices for modern networks and still do not push any proprietary technology inside, which I like the most.
Take a look here for Layer 2 features on SRX240:
http://www.juniper.net/techpubs/en_US/junos10.4/information-products/topic-collections/security/software-all/layer-2/index.html
73: Comment Link
SSG is very old now and EOL. You should use a Juniper SRX, these are the replacement.
The SRX300 is the latest model that replaces the SRX100 and SSG5.
75: Comment Link
Even though the SSG are end of life. The can be purchased on ebay with good prices($25 to $50). This makes it affordable for home users. Most home user are not going to spend hundreds of dollar on enterprise firewall from a tier I vendor like Juniper. I been relying on the desktop PC firewalls. Now I can put in a enterprise firewall at home. It just takes some time to download their documentations to learn how to configure them. They are still available for download on Juniper's website. I almost purchased a Cisco ASA 5505 with 50 user license but decided to go with Juniper SSG5 which has unlimited user.
76: Comment Link