Sat, 23 Aug 2014 12:37 AM
JunOS 12.1X47, first gen SRX devices are no longer supported
Michael Dale
ERROR: Unsupported platform srx210h for 12.1X47 and higher
This is the error that you will get if you try and install 12.1X47 on a Juniper SRX 210H (or 100B, 100H or any "first gen" srx).
From reading:
http://www.juniper.net/techpubs/en_US/junos12.1x47/information-products/topic-collections/release-notes/12.1x47/index.html?topic-87511.html
"Note: Upgrading to Junos OS Release 12.1X47-D10 or later is not supported on the J Series devices or on the low-memory versions of the SRX100 and SRX200 lines."
I thought maybe it would just be the base memory devices e.g SRX100B or SRX210B but it looks like any SRX device with 512MB or 1GB ram are not supported.
This is a shame as for example the SRX110H devices weren't that old and supported removable/upgradable CF cards. Even the SRX240B2 is not supported! You need 2GB of ram.
The ASA5505 is good example of a device designed to last. Pity I like JunOS so much!
I have a couple of SRX240Hs, these allow you to upgrade the ram (standard DDR2), so I wonder if an upgraded 240H will work.
Sun, 08 Aug 2010 10:53 AM
Cisco Fail
Michael Dale
I don't normally sell Cisco products, but one of my clients already has a full Cisco network, so for them we purchased an ASA5505 for a remote office.
Cisco have made a number of upgrades to the software of the ASA range and have really stuffed up a few sections.
- It took me about a month to get a new ASA5505 (the new 512mb version as the OS now needs more memory)! For some reason Cisco cannot manage their stock, they suck. Also the ASA5505 should have had 512mb to start with.
- Finally when the ASA5505 comes, it doesn't work! It doesn't even switch on. I don't think I've ever had a DOA Juniper product. I understand these things happen but it doesn't leave a good impression.
- The power connector is really bad, it is some stupidly small plastic thing that will no doubt break in the future.
Overall the ASA5505 is a good product, but they've done some stupid things with the range. I wouldn't recommend one over a Juniper SSG.
I don't know why companies always create shitty products, the Juniper SRX range is another fine example. The code base on the Juniper SRX is still buggy. Junos 10.2 should finally fix most of my issues with the OS, but really.
Thu, 21 Feb 2008 12:09 PM
Cisco ASA 5505 vs Juniper SSG 5
Michael Dale
I thought it was about time I did proper review of the Cisco ASA 5505 and the Juniper SSG 5.
Both devices are at the low end of firewall security devices offered by Cisco and Juniper.
The ASA 5505 is part of Cisco's new range of Adaptive Security Appliances (ASA) the replacement for the PIX. The 5505 replaces the old PIX 501 and 506e.
The SSG 5 is Juniper's lowest end Secure Services Gateway (SSG). The SSG 5 replaces the old Netscreen 5GT.
There are many models of the SSG 5 and ASA 5505 available, for this review I will be looking at the non wireless SSG 5 256mb version and the unlimited user ASA 5505 K9 version.
Before we get started I should make it clear that I work with the Juniper range of hardware every day; so I may be bias.
Overview
The first thing I'll do is compare the two devices "on paper".
| Cisco ASA 5505 | Juniper SSG 5 | |
| Model | ASA5505-UL-BUN-K9 | SSG-5-SH SSG5 RS-232 256MB |
| RRP* | $AU1,681.90 inc GST | $AU1,125.00 inc GST |
| Firewall Throughput | 150 Mbps | 160 Mbps or 90 Mbps of IMIX** traffic |
| VPN Throughput | 100 Mbps | 40 Mbps |
| Sessions | 10,000 | 8,000 |
| Connections/Second | 4,000 | 2,800 |
| Packets Per Second (64 byte) | 85,000 | 30,000 |
| IPSec Tunnels | 10 | 25 |
| SSL Tunnels | 2 | N/A |
| Memory | 256 MB (upgradable) | 256 MB |
| Flash | 128 MB (upgradable) | 64 MB (fixed) |
| Ethernet Ports | 8x100 Mbps (2 of which are PoE) | 7x100 Mbps |
| USB | 3xUSB 2.0 | 1xUSB 1.1 |
| VLANs | 3 (trunking disabled, DMZ Restricted) | 10 |
| OS | ASA 8.0(2) - ASDM 6.0(2) | ScreenOS 6.1.0r1 |
| Users | Unlimited | Unlimited |
| Routing Protocols | RIP v1/v2, OSPF, EIGRP | RIP v1/v2, BGP, OSPF |
| Anti-Virus | No (possible future) | Yes (paid for subscription) |
| Deep Inspection | Yes | Yes |
| Anti-Spam | No (possible future) | Yes (paid for subscription) |
| Console | RJ45 | RJ45 |
| Dialup Modem | No | No (external modem can be connected via the AUX port) |
| IPv6 | Yes | Yes |
* RRP based on Ingram Micro's pricing
** IMIX traffic is more demanding than a single packet size performance test and as such is more representative of real-world customer network traffic.
The IMIX traffic used is made up of 58.33% 64 byte packets + 33.33% 570 byte packets + 8.33% 1518 byte packets of UDP traffic.
So on paper the ASA 5505 has much better throughput and general hardware specifications, yet the SSG 5 supports more VPN tunnels, VLANS and has full UTM (Unified Threat Management).
The ASA 5505 is also about 50% more expensive (based on the retail prices), saying this wholesale prices of the two devices only differ by about $250 ext GST.
Cisco ASA 5505 out of the box
The ASA 5505 comes with the following:
- ASA 5505
- Power Supply
- Getting Started Guide (Software Version 7.2)
- Rollover console cable
- 90-Day Hardware Warranty
- Software and Documentation CD (Software Version 7.2)
- Regulatory Compliance and Safety Information Booklet
- 2 Ethernet Cables
Juniper SSG 5 out of the box
The SSG 5 comes with the following:
- SSG 5
- Power Supply
- Serial to RJ45 connector
- 1-Year Hardware Warranty
- 90-Day Software Warranty (from the date of shipment)
- Free download of the latest ScreenOS for the first 90-Days
- Software and Documentation CD
- 1 Ethernet Cable
- Desk Stand (allows the SSG 5 to stand upright)
The 90-Day software download for the Juniper device means that you can have to the latest software when you first purchase the device. Unfortunately this time period starts from when the device leaves Juniper. So if you purchase the device from a reseller the software update period may have already expired. This is still better than Cisco that requires you to purchase a SmartNet agreement before you can download anything.
The 90-Day Cisco hardware warranty is also a bit rude.
Cisco ASA 5505 Starting it up
Out of the box the ASA is setup with Ethernet0/0 being the WAN side while the rest of ports are setup as the LAN side. The default IP address of the box is 192.168.1.1.
If you're running an internet connection where an ip address is handed out via DHCP then the ASA will give you basic internet access straight off, although most of the time you'll want to configure PPPoE or something.
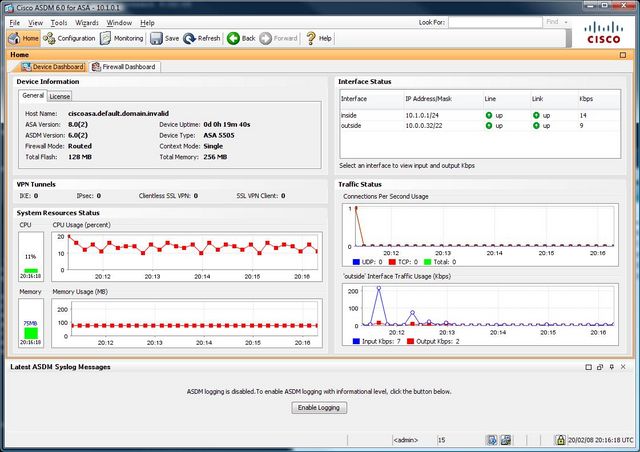
For users who have not used Cisco gear before then the easiest way is through ASDM (Adaptive Security Device Manager), cisco's GUI setup interface. To access this browse to https://192.168.1.1/ and download the ASDM.
Once started you are greeted with some statistics of the ASA.
ASDM is up to version 6 and is it now fairly comprehensive; if you don't like the command line then most of the configuration can be done here.
By default the ASA blocks and filters certain traffic for example ICMP is blocked.
Juniper SSG 5 Starting it up
Out of the box the SSG 5 is setup with Eth0/0 being the WAN side, Eth0/1 being the DMZ and the rest of the ports being the LAN side. The default IP address of the box is 192.168.1.1.
The SSG 5 uses zones.
"A security zone is a collection of one or more network segments requiring the regulation of inbound and outbound traffic via policies. Security zones are logical entities to which one or more interfaces are bound."
So what Cisco call VLANs (or Security Levels) are basically what Juniper call Zones.
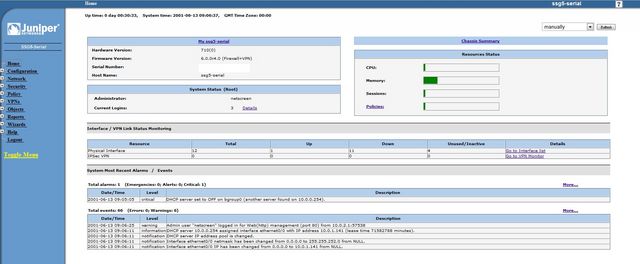
The SSG is managed through a web interface this can be found at http://192.168.1.1 (default username and password: netscreen).
Once you've logged in you are greated a general overview of the device.
Like the cisco device the SSG also allows configuration via the command line; although the WebUI is much more complete than the Cisco ASDM.
Personally I do most of my configuration in the WebUI.
By default all outbound traffic is allowed and the WAN interface (or Untrust as Juniper call it) is set in NAT mode. The Untrust interface isn't setup to receive an address via DHCP by default.
Cisco ASA 5505 The Hardware
The physical construction of the 5505 is very good. The outside casing is mostly plastic, while the base of the system is metal. The only point of concern is the power connector; it seems a bit flimsy and could be easily broken.
If you open up the 5505 you can see that both the flash and ram is upgradable. The flash is just a standard compact flash card, while the ram is PC3200 DDR UB NON-ECC CL3 DIMM 2.5v or 2.6v. It looks like the ASA 5505 can support up to 512mb of Ram.
The primary CPU is based on an AMD Geode chip, plus there is a hardware acceleration chip too (for VPN encryption etc).
The 5505 also has a Security Services Card slot allowing extra functionality to be added on. Although there are not any cards at this stage.
There are 2 USB 2.0 ports on the back and 1 on the front. Seems like a lot for a firewall! At this stage they don't do anything.
The inclusion of two Power over Ethernet ports is a great idea as it allows you to simply plug an IP phone in without the need for an extra power brick.
There is an internal battery that can be replaced if required.
Overall the ASA 5505 feel like it was built to last.
Juniper SSG 5 The Hardware
The physical construction of the SSG 5 is good, but it isn't has good as the 5505. My main point of concern is the single USB port on the back. It isn't attached to the outside casing and just feels a bit flimsy.
The SSG 5 allows for the memory to be upgraded, although 256mb is the max. I tried a 512mb DDR2 SODIMM in the device but it didn't boot. It is possible that I was using the wrong type of ram (on second look it may need DDR1). The flash memory is soldered onto the board and cannot be replaced.
The SSG 5 uses an Intel IXP455 chip running at 533MHz.
There is a single USB 1.1 port on the back of the device that can be used for storing log files or other firmware.
Cisco ASA 5505 The Software
At the time of writing software version 8.0(3) is currently the latest version for the ASA. Unfortunately I currently only have 8.0(2), saying this the differences should only be bug fixes.
The ASA software is simply a continuation of the PIX software. The configuration is stored in a single text file. With each version of the ASA/PIX software the command line configuration is slowly becoming more and more like Cisco IOS which is not a bad thing.
The ASA has a stack of features for a device so small and cheap. It does everything that the PIX 506e does (IPsec VPN, SPI firewall etc) plus more (SSL VPN, EIGMP). The inclusion of SSL VPN means that this device can easily support teleworkers that may not have access to an unrestricted internet connection. SSL VPN gives the end user an option of a client based connection (similar to an IPsec VPN) or a clientless connection (a web portal to published files and services).
The ASA 5505 also provides basic routing and nat functionality, meaning that you can run this device without a separate router. Unfortunately there is no option for an integrated ADSL modem, so a modem will need to be purchased.
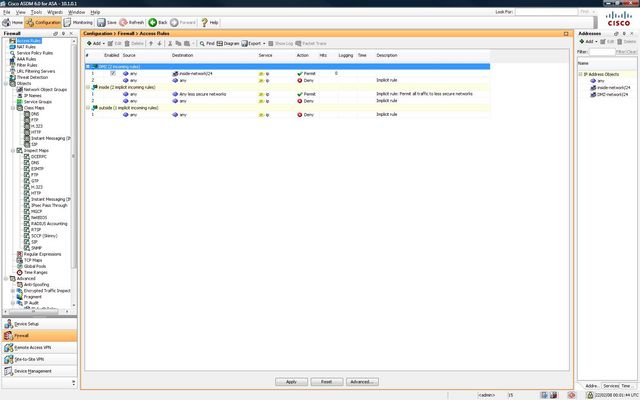
The configuration of the ASA can be scary for new users. ASDM is not particularly well laid out. NAT rules are in a different location to access rules and everytime you want to make a change you must save and upload the configuration again. The base license is also restrictive, you are limited to three "zones": untrust, trust and dmz. You cannot create pin holes in the DMZ to allow access the the Trust network either.
The SSL VPN is also very limited as you are only allowed 2 SSL VPN connections. IPsec is a little better with 10 tunnels allowed, but even cheap SOHO routers can do 10 IPsec tunnels.
All of these limits can be removed or increased with more expensive licenses, but they are much much more costly.
It is possible to get the ASA 5505 in 10 and 50 user versions (number of computers using the internet behind the ASA). Why Cisco have this limit is beond me. I've never seen a cheap SOHO router with a user limit.
The reporting options in ASA 5505 are fantastic. If you want to know what is going on it your network then the ASA will tell you. It can display the most used services, sources or destinations in a pie chart (plus a whole stack of other options).
Overall the ASA software is good, but there are far too many limits on the base 5505.
ASA Software Version 8.1 is due soon although I've yet to hear what extra features it will include.
Juniper SSG 5 The Software
The SSG 5 came out with ScreenOS 5.4 but since then Juniper have released 6.0 and 6.1 both adding lots of extra functionality. ScreenOS supports just about any routing protocol (BGP, OSPF, RIP etc) and has some really nice features that aren't found on the ASA 5505.
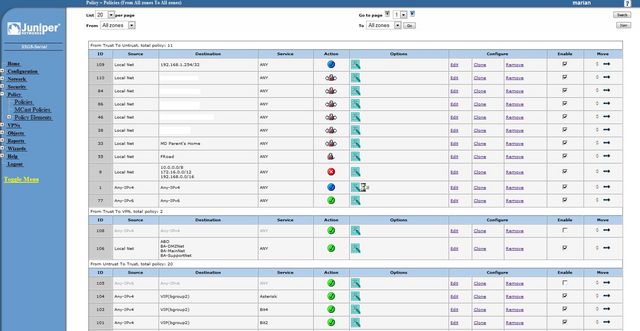
The base SSG 5 license supports unlimited users, 25 VPN tunnels and 10 zones. The extra zones really makes the SSG 5 stand out. For example you can have a Untrust, Trust, DMZ and VPN zone. All VPN tunnels can be bound to the VPN zone, separating it from internet traffic. There are also no limits on how the zones work so the DMZ can talk to the any zone if you so wish. With 10 zones every port on the SSG 5 can be part of a different network. So if I wanted to add a wireless access point I could create a zone that only allows the wireless users to access the internet.
Policy management is also much better than the ASA. Every change made via the web interface is automatically saved. You can quickly disable policies and move them around. You can fine tune each policy. For example you might want to enable NAT on a policy, or add anti-spam scanning on certain incoming SMTP connections. The policy management on the SSG 5 feels much more mature.
Again the SSG 5 like the ASA 5505 can be used as a stand alone device without the need for an extra router. The SSG 5 does have another nice option, you can purchase them with ADSL2+ modems built in (or ISDN or 56k modem). So you don't need to buy an extra modem. Saying this I find it easier and cheaper just to use an external modem as it can be upgraded if a new technology comes out.
ScreenOS 6.0 added Auto Connect VPN which works the same as Cisco's Dynamic Multipoint Virtual Private Network. This basically means that in a hub and spoke vpn setup the spoke sites (remote offices) can automatically establish a VPN tunnel between each other (based on the rules at the hub) to reduce the traffic going through the hub. This can increase bandwidth and decrease latency.
ScreenOS 6.1 added IKEv2 the next version of the Internet Key Exchange protocol which is used in IPsec.
UPDATE: Power Adapter
Just thought I'd add a quick section on the power adapter.
The Cisco ASA 5505's power adapter is quite large and seems to make a bit of noise (more than the device itself).

Conclusion
Both devices are fantastic yet each have their own strengths and weaknesses. For example the SSG doesn't support SSL VPNs while the ASA doesn't support built in Anti-Virus or Anti-Spam.
I feel that the ASA 5505 is a little let down by its software and licensing limits. The reporting options in the ASA are much better then the SSG, but this doesn't make up for its other short comings. SSL VPN is nice but again far too limited with only 2 connections. The ASA 5505 hardware is clearly better than the SSG 5: PoE ports, USB 2, higher throughput.
On paper the SSG 5 isn't has good as the ASA 5505, yet the device is much less limited. I personally don't feel that the performance of the SSG 5 isn't an issue. These two devices are designed for small businesses and teleworkers, they're never going to see 150mbit/sec of traffic.
The SSG 5 comes with many more hardware options, you can even get a version with 802.11a/b/g wireless.
To me the SSG 5 makes a better router than the ASA 5505. While the ASA 5505 makes more sense for a business with teleworkers that require SSL VPN.
The SSG 5 can handle more VPN tunnels (up to 40 with an extended license) and has some technology that makes it better for site to site VPNs, such as running BGP over an IPsec tunnel.
If you're currently running a Cisco network stick to the ASA. Likewise if you're running a Juniper network use the SSG.
For new users you need to decide on what is important to you. Do you plan on using SSL VPN? Then get the ASA 5505. If you're just using IPsec or require some more complex networks/routing get the SSG 5.
Value for money? The SSG 5 is better as there are far less software limits.
Tue, 15 Nov 2005 6:54 PM
I've done some basic IPv6 stuff in the past, which only involved a single IPv6 address and a connection to aarnet. I was going to look into setting up a tunnel on my router (a m0n0wall box) so that I had both a IPv4 address and a IPv6 address but it didn't support IPv6 stuff.IPv6 again!
Michael Dale
Anyway I've got my cisco 2651 up and connected to the internet and it has full IPv6 support so I decided to give it a go. Aarnet also give you an option to run a full /64 subnet, so I decided to give it a go.
The web interface outputs a shell script that gives you the configuration needed for the router. So I modified by config (with some small changes).
ipv6 unicast-routing
!
interface tunnel0
ipv6 address 2001:0388:f000:0000:0000:0000:0000:0247/128
tunnel source dialer1
tunnel destination 202.158.196.131
tunnel mode ipv6ip
!
ipv6 route ::/0 tunnel0
!
interface FastEthernet 0/0
ipv6 address 2001:0388:c148:1::/64 eui-64
ipv6 nd prefix-advertisement 2001:0388:c148:1::/64 43200 43200 onlink autoconfig
!
The last section (prefix-advertisement) is similar to DHCP, it assigns an IPv6 address to any IPv6 capable computer/OS. So both my Windows 2000 box (with IPv6 kit installed) and Mac OS X system were given a full routed IPv6 address. No dodgy natted connection here, a full routed /64 subnet. :)
The speed of the IPv6 is pretty good seeing as it is running through an aarnet tunnel.
electra:~ michaeldale$ ping vee-six.telstra.net
PING vee-six.telstra.net (203.50.0.254): 56 data bytes
64 bytes from 203.50.0.254: icmp_seq=0 ttl=56 time=21.330 ms
64 bytes from 203.50.0.254: icmp_seq=1 ttl=56 time=19.761 ms
64 bytes from 203.50.0.254: icmp_seq=2 ttl=56 time=21.125 ms
64 bytes from 203.50.0.254: icmp_seq=3 ttl=56 time=19.949 ms
^C
--- vee-six.telstra.net ping statistics ---
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max/stddev = 19.761/20.541/21.330/0.693 ms
electra:~ michaeldale$ ping6 vee-six.telstra.net
PING6(56=40+8+8 bytes) 2001:388:c148:1:211:24ff:fe2a:f1b3 --> 2001:360::3
16 bytes from 2001:360::3, icmp_seq=0 hlim=58 time=25.059 ms
16 bytes from 2001:360::3, icmp_seq=1 hlim=58 time=25.874 ms
16 bytes from 2001:360::3, icmp_seq=2 hlim=58 time=23.465 ms
16 bytes from 2001:360::3, icmp_seq=3 hlim=58 time=24.281 ms
^C
--- vee-six.telstra.net ping6 statistics ---
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max = 23.465/24.670/25.874 ms
electra:~ michaeldale$ traceroute6 vee-six.telstra.net
traceroute6 to vee-six.telstra.net (2001:360::3) from 2001:388:c148:1:211:24ff:fe2a:f1b3, 30 hops max, 12 byte packets
1 2001:388:c148:1:207:eff:fe80:5cc0 2.565 ms 1.756 ms 1.422 ms
2 2001:388:f000::246 25.438 ms 17.068 ms 19.847 ms
3 gigether0-2-0.bb1.a.syd.aarnet.net.au 37.864 ms 27.464 ms 22.706 ms
4 gigabitethernet3-0.bb3.a.syd.aarnet.net.au 28.522 ms 19.571 ms 17.456 ms
5 eth0.ipv6.broadway.aarnet.net.au 25.852 ms 16.863 ms 19.326 ms
6 2001:388:200:4::2 25.896 ms 23.23 ms 25.435 ms
7 2001:388:200:4::2 26.875 ms !P 23.721 ms !P 27.306 ms !P
And a trace to my mac (the second last hop is my cisco router) from here
traceroute6 to 2001:388:c148:1:211:24ff:fe2a:f1b3 (2001:388:c148:1:211:24ff:fe2a:f1b3) from 2001:1888:0:1:290:27ff:fe9a:4b0b, 64 hops max, 12 byte packets
1 puaiohi-fe1-0-1 1.761 ms 1.923 ms 1.961 ms
2 akepa-e0-0-7 2.737 ms 2.865 ms 2.922 ms
3 tunnel-henet-ca-us 62.519 ms 62.382 ms 62.737 ms
4 3ffe:81d0:ffff:1::1 61.172 ms 61.049 ms 61.039 ms
5 3ffe:80a::b1 63.145 ms 61.613 ms 63.022 ms
6 10gigether0-0-0.bb1.a.syd.aarnet.net.au 237.385 ms 227.818 ms 254.435 ms
7 broker1.a.syd.aarnet.net.au 222.550 ms 222.128 ms 223.146 ms
8 2001:388:f000::247 240.004 ms 238.553 ms 240.206 ms
9 2001:388:c148:1:211:24ff:fe2a:f1b3 241.638 ms 240.077 ms 239.622 m